Normally, it is often reported that once a company is compromised or breached, attackers hide in the internal networks and systems for months before being detected. But… How do they initially infiltrate? How do they move within the network? And how do they find or steal sensitive information?
Today, we are back from a few days off and want to talk about the “ATT&CK” matrix created and maintained by MITRE. But wait… What is MITRE?
The MITRE Corporation is a non-profit American organization aimed at improving national security. It focuses on critical areas such as cybersecurity, defense, health, and aviation. To achieve this, they collaborate with public and private organizations to address challenges and provide solutions that serve the public interest.

Their most well-known contribution in the field of cybersecurity is ATT&CK.
Commonly known as the MITRE attack matrix, it is an acronym that stands for “Adversarial Tactics, Techniques and Common Knowledge”. If we translate it, we could speak of something like Tactics, Techniques and Common Knowledge of the Adversary. And we are really talking about a knowledge base that compiles the techniques used by the bad guys during their attacks. This information, moreover, is based on data obtained during real attacks that have occurred. In other words, we are not talking about assumptions or theoretical concepts, we are talking about the actual behavior of criminals during the different stages of the life cycle of an attack.
This information is categorized in a matrix whose perspective is the attacker’s targets. The columns reflect the tactics, which would reflect the attacker’s high-level objectives. Some of the attacker’s objectives could be:
- To look for potential victims, reflected in the Active Scanning techniques, or Active Scanning.
- To sneak into the company, reflected in the tactic Initial Access, or Initial Access.
- Moving through the network, reflected in Lateral Movement, or Lateral Movement.
- Stealing information, reflected in the Exfiltration column.
Within each column there is a series of rows that reflect the techniques, that is, the different ways the attacker has to reach a desired target. It is important to understand that attackers have different mechanisms to achieve the objectives, depending on their own experience, the tools they have, or how they adapt to the particular characteristics of your company.
Each technique in the matrix has a description of the method, the platforms affected, and known groups of criminals known to have used that technique in actual attacks.
Let’s take an example to understand it better: the Reconnaissance stage.
Reconnaissance is the initial stage where attackers gather information about their target before executing the attack. They perform different activities aimed at collecting information that can help in future attacks. For example, finding data about the organization such as its website, infrastructure details, employee information, or its vulnerabilities.
The first technique mentioned in this category is Active Scanning. In this case, the attacker actively searches across the Internet or a specific organization to identify information that allows for subsequent attacks, such as misconfigured or vulnerable systems. As we will see, this is one of the most commonly used techniques by adversaries to find new victims on the Internet.
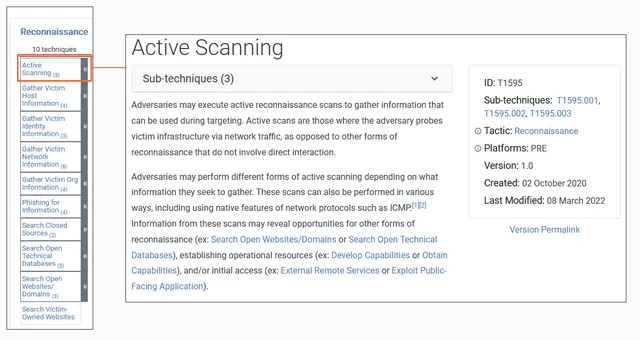
Within this technique, we can see, as reflected in the far-right box, that there are also three sub-techniques:
- T1595.001: Scanning IP Blocks
- T1595.002: Vulnerability Scanning
- T1595.003: Wordlist Scanning
The first two, for example, refer to the continuous scanning of public IP address ranges, searching for exposed systems and the software they are running, as well as looking for vulnerabilities in the detected software.
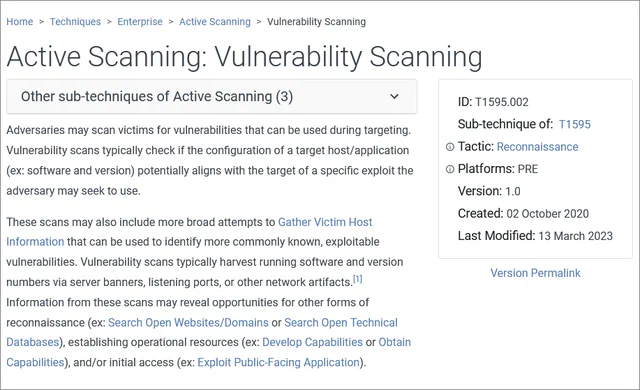
On the associated page, examples of real attackers known to have used these techniques to find new victims are also listed.
Knowing that attackers continuously look for vulnerabilities across the Internet, we can adapt our company’s security measures. For example, by scanning our own systems exposed to the Internet to ensure that none are affected by known vulnerabilities, and if they are, correcting them immediately before an attacker can exploit those vulnerabilities.