A few days ago, we learned the news that the leader of the cybercriminal group LockBit 1, one of the largest malicious actors dedicated to ransomware, had been unmasked. But… What is ransomware, and how do these scams work?
What is Ransomware?
Ransomware is a type of malware designed to encrypt a victim’s files, making the data inaccessible. Subsequently, attackers demand a ransom, usually in cryptocurrencies, in exchange for the decryption key that can unlock the encrypted files or systems 2.
Ransomware attacks are the fastest-growing form of cybercrime in recent years. Additionally, they affect organizations of all sizes, including small and medium-sized enterprises (SMEs) 3.
Next, we will explore the attackers’ methodologies, their consequences, and how SMEs can deal with these attacks.
Tactics of Malicious Actors
Cybercriminals operating ransomware use various tactics:
- Anonymity: They hide their identity using cryptocurrencies, the deep web, and other anonymous networks to make tracking difficult.
- Surprise effect: By persisting in infected systems and actively researching the victim, they manage to execute the attack (data encryption) at the most painful moment, such as on weekends, holidays, or during the backup process.
- Double extortion: Some ransomware variants, and increasingly more criminal groups, not only extort with the data ransom but also threaten to leak stolen information if the ransom is not paid, adding additional pressure.
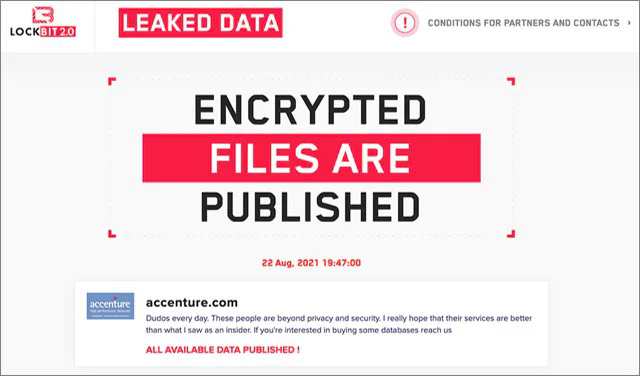
Identifying a Ransomware Attack
In summary, a ransomware attack consists of the following stages, as outlined by the MITRE attack matrix:
1. Reconnaissance
In this phase, cybercriminals perform various activities to gather information about the potential victim. They usually scan the Internet for systems with unpatched or unknown vulnerabilities. If they detect a potential victim, they use processes to better identify their target. Some of these techniques include:
- Social engineering: Cybercriminals try to learn more about their victims through phishing emails, pretexting, phone calls, or in-person interaction.
- Attack surface exposure: They locate network systems exposed on the Internet, scan their open ports for vulnerabilities, and discover other elements on the network.
- Open source intelligence (OSINT): Using OSINT techniques, they obtain information about who their victim is, what their business is, who their clients are, and what their pain points are.
2. Initial Compromise
To gain access to systems, there are various methods, but the most common are:
- Credential theft: Attackers obtain credentials through phishing or social engineering techniques and then use them to access systems with standard protocols, such as Remote Desktop Protocol (RDP).
- Malware: Whether through email or malicious URLs, attackers manage to execute malicious code on systems to infiltrate them.
- Vulnerabilities: They exploit known unpatched vulnerabilities or zero-day vulnerabilities to gain access to systems.
3. Persistence, Privilege Escalation, and Lateral Movement
After the initial compromise, cybercriminals take measures to maintain access to the target network for a prolonged period. The goal of persistence is to ensure continued access to the victim’s network even if the initial compromise is detected and corrected.
Once attackers establish persistence in the systems, they use the following days to try to elevate privileges in the organization until they compromise administrative accounts. Similarly, they attempt lateral movements, i.e., they move through the victim’s network to gain as many accesses as possible and cause the maximum possible damage to the victim.
All this is done as quietly and undetectably as possible.
4. Information Gathering
To create high-impact attacks and demand a higher ransom, attackers will conduct a thorough reconnaissance of the victim, understanding the organization, where the most critical systems are, what times and how backups are performed, etc.
They will also begin to identify and filter valuable data before encrypting it, such as databases that may contain critical information like intellectual property, financial records, personal data, or customer data.
5. Malware Execution
It is the last opportunity for security teams to prevent the attack. If it has not been possible to detect and isolate the cybercriminals up to this point, they will end up executing the malware. But first, they usually take measures to ensure everything works perfectly and cover their tracks:
- Delete logs to prevent forensic analysis.
- Modify and customize the encryption malware code to adapt it to the victim.
- Check communications with their Command & Control (C&C).
- Delete and destroy backups.
6. Extortion
The moment when attackers execute the ransomware and notify the victims that their data has been encrypted, in most cases, preventing the company from accessing its critical systems until a ransom is paid.
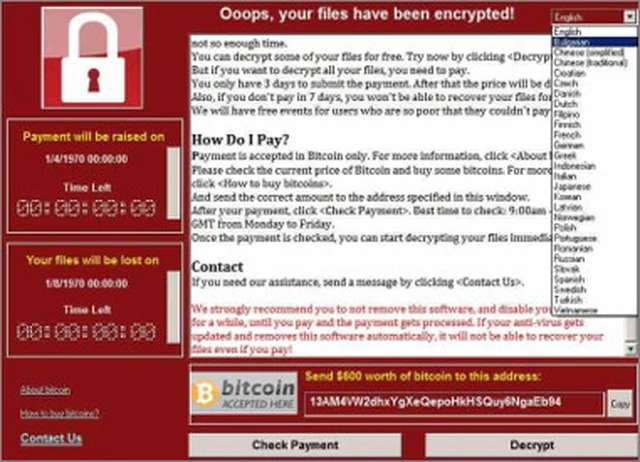
Unfortunately, for most companies, this notification and extortion message is the first indication of a ransomware attack. When this happens, it is usually too late.
Impact on SMEs
Generally, the lack of resources or their limitation makes SMEs particularly vulnerable to these types of attacks. Often, the lack of adequate security measures aggravates the consequences:
- Economic losses: Correcting and remediating such an attack can be very costly for an SME, but due to the interruption of their operations, their revenue sources are also affected, making the economic damage double.
- Reputational damage: Additionally, a ransomware attack can erode customer trust and affect the company’s image.
It is worth noting that 25% of organizations affected by a ransomware attack are forced to close within 6 months4, but for small businesses, the percentage increases to 60%5.
That is, 3 out of 5 small businesses that suffer a ransomware attack are forced to close after the incident. Undoubtedly, these are brutal attacks with chilling numbers.
How Do I Protect Myself?
To protect against ransomware, it is necessary to adopt proactive measures such as:
- Regular backups: Perform regular backups that should be stored out of attackers’ reach.
- Invest in cybersecurity: Implement security solutions and processes within the company to help monitor systems, identify exposure on the internet, as well as known vulnerabilities, and work to remediate them. Keeping software updated is crucial.
- Awareness: Train employees on safe practices, knowing how to recognize phishing emails can greatly prevent these infections.
Conclusion
Ransomware is a very real threat to organizations, particularly SMEs. By understanding the risks and taking preventive measures, companies can protect their data and stay “safe” from cyberattacks.
https://nationalcrimeagency.gov.uk/news/lockbit-leader-unmasked-and-sanctioned ↩︎
https://www.fortinet.com/content/dam/fortinet/assets/reports/report-2023-ransomware-global-research.pdf ↩︎
https://www.newsweek.com/most-businesses-that-pay-off-after-ransomware-hack-hit-second-attack-study-1601266 ↩︎
https://cybersecurityventures.com/60-percent-of-small-companies-close-within-6-months-of-being-hacked/ ↩︎