Integrating security into the Secure Software Development Lifecycle (sSDLC) is key to protecting applications, reducing risks in the software supply chain, and complying with regulations such as NIS2, DORA, or the Spanish Esquema Nacional de Seguridad (ENS).
It is no longer enough to review code at the end: cybersecurity must be present from the very first commit.
Benefits of integrating security into the SDLC:
- Fewer vulnerabilities in production.
- Compliance from the design stage.
- Reduced remediation costs.
- Visibility into real, prioritized risks.
Most modern organizations develop software, even if their main business is not technology. Internal automations, customer platforms, cloud microservices, mobile applications, or open APIs are part of everyday operations. However, while development cycles have accelerated thanks to agile methodologies and CI/CD tools, security often still operates like it did in 2010: ad-hoc interventions, late reviews, and little context on the real risks.
In this context, attacks on the software supply chain have grown alarmingly. It is much easier to compromise a dependency shared by hundreds of organizations than to attack them one by one. And worse: many companies don’t even know which libraries they are using, what configurations are embedded in their containers, or what secrets may have been unintentionally leaked in their repositories.
Comprehensive security in the Software Development Lifecycle (sSDLC)
Talking about security in the SDLC or sSDLC is not limited to reviewing source code. Modern software is built from assembled components: proprietary code, third-party libraries, containers, infrastructure-as-code scripts, cloud configurations, external services, etc. Each of these elements can introduce risks.
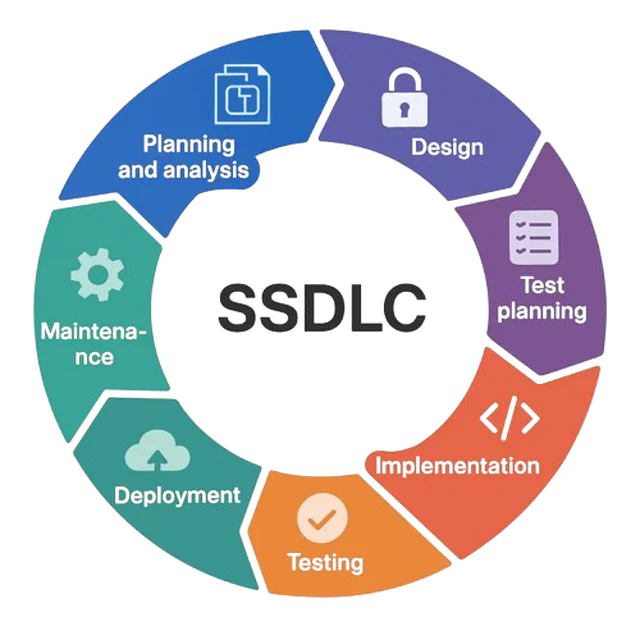
A continuous security in software development approach means analyzing and monitoring all these components in an integrated way, from the first commit to the running environment.
This includes:
- Static Application Security Testing (SAST) from the developer’s environment.
- Software Composition Analysis (SCA) to detect vulnerabilities in dependencies and generate updated SBOMs.
- Infrastructure-as-Code (IaC) review to avoid insecure configurations from the design stage.
- Detection of exposed secrets and credentials in code, pipelines, or containers.
- Container image scanning and cloud configuration review (CSPM).
- Automated compliance reports for standards such as SOC 2, OWASP Top 10, NIS2, etc.
What matters is not just having these capabilities, but ensuring they are connected, run automatically, and produce useful, prioritized, and actionable information.
Reducing false positives and alert fatigue in application security
One of the biggest challenges in application security is excessive noise. If a developer receives dozens of vague alerts in every review, they are likely to ignore them. This is why a modern platform must be able to understand the real context of each finding: whether the vulnerable code is actually executed, if the affected library is active in production, if the leaked secret is in use, etc.
The combination of artificial intelligence, custom rules, and deduplication engines reduces false positives and focuses attention on what really matters. This not only improves actual security but also fosters collaboration between development, security, and compliance teams.
NIS2, DORA, and ENS: security requirements in software development
European regulation is evolving rapidly. NIS2, which will come into effect nationally in 2025, requires essential and critical sector companies to implement technical measures to ensure information security, including the software they use and develop. One key aspect is risk management in the supply chain.
DORA, in turn, applies to the financial sector and requires evidence of controls over technology providers and the digital components they use. Among its requirements are code traceability, vulnerability identification, and the ability to respond quickly to incidents.
The National Security Framework (ENS), already in force in Spain for public entities and many private organizations working with the Administration, reinforces these same principles: configuration control, security in development, and periodic software reviews.
All these regulations agree on one thing: the SSDLC and secure development are not just best practices—they are a technical and legal obligation.
How Flameera integrates continuous security and compliance into the SDLC
At Flameera, we help organizations incorporate security into their SDLC in a realistic and sustainable way. We do this through three pillars:
- Maturity assessment: identifying critical points in the current development flow.
- Continuous security integration: connecting tools that cover from code to the cloud environment, prioritizing based on real risk.
- Support in regulatory compliance: generating technical evidence, SBOMs, and reports to facilitate audits and reviews.
Our approach adapts to any type of technology stack and fosters collaboration between teams without slowing down delivery. With Flameera, companies implement an SSDLC that combines continuous security, regulatory compliance, and operational efficiency.