As we already know, small and medium-sized enterprises (SMEs) are increasingly being targeted by cybercriminals. Despite their smaller size, SMEs possess equally valuable data and assets for criminals, making them lucrative prey. However, they typically have significantly lower protection measures and resources compared to large companies. This makes them easier targets, where the simplicity of attacking and obtaining a return skyrockets.
For this reason, we would like to give a brief reminder of the specific threats that SMEs face and offer some tips to help you defend against these dangers.
Phishing Attacks: The Silent Killer
We all know phishing. We have all received fraudulent messages, both in our professional and personal lives. However, they remain one of the most prevalent threats in the business world today.

SMEs are not exempt from this risk, and the lack of training and awareness among employees poses a serious threat to this type of attack. Cybercriminals continue to impersonate legitimate entities, such as banks and other well-known companies, to deceive unsuspecting employees into revealing sensitive information or clicking on links that lead to malicious sites. Phishing comes in the form of emails, SMS, or social media messages.
By the way, did you know there is a concept called Spear-Phishing? It is a more advanced and sophisticated type of phishing, where the attack is not directed at all users with generic messages but targets one or several very specific individuals after investigating them, making it much more dangerous.
Ransomware: Hostages of the 21st Century
Nowadays, it is almost impossible not to have heard about these types of attacks, which represent a significant threat to any business, especially SMEs, and can have very dangerous consequences for those who suffer from them.
In this type of attack, cybercriminals gain access to a company’s network, and once they have access to their information, they encrypt it completely, making all the data inaccessible to the owner. Then, they demand a ransom in exchange for the decryption key.
Previously, criminals would contact the company and threaten to permanently delete the data if the payment was not made. Later, adapting to companies with external backups, cybercriminals began to threaten to publish the information directly on the Internet if the payment was not made by a specific date, exposing the company to reputational, regulatory, and competitive risks, as anyone could access your internal system information.

Internal Threats: A Trojan Horse in Your Network
Traditionally, external threats have received the most attention from risk managers in companies. After all, the attacker is outside… right?
The reality is that internal threats can be even more damaging. Internally, we can categorize threats into two categories:
- Unintentional threats, such as those arising from negligence or human error. For example, an employee losing a device with sensitive corporate information or mistakenly sending sensitive information in an email to the wrong address.
- Intentional threats. Generated by a malicious insider, the most typical example being a disgruntled employee who sabotages the company internally, steals confidential information, etc. They can be extremely dangerous because they may know the company and its weaknesses perfectly.
It is also important to recognize internal threats that third parties can cause, such as employees of a supplier working within the company, even if they are not part of it.
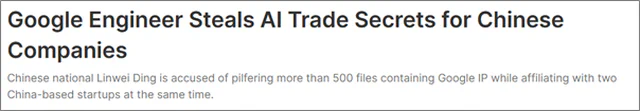
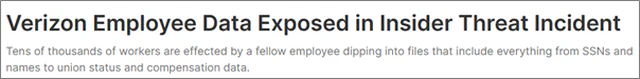
This is a risk that still lacks awareness. We have spent years warning of this risk to managers of all types of companies, leading to disagreements with technical and management teams alike. Unfortunately, time has proven us right, and the risk has materialized.
Data Breaches: Notifications to the AEPD
One day you are informed that someone has stolen data from the company, and now you have to analyze the incident:
- How did it happen?
- What data was affected? Was it confidential business data, or were there also personal data of customers?
- Do I have to notify someone? How should I do it? To whom exactly? How much time do I have to do it?
- How do I recover the company’s activities?
- How can I prevent it from happening again?
These and many other questions make this scenario one of the worst for any SME. Let’s not forget the economic impact of recovering from the security incident, the consequences for the company’s reputation, and, finally, the potential sanctions that could be applied to your business.

Protect Your Business: The Path to Resilience
Although all these threats can scare many SMEs, fortunately, there are measures that can be taken to prevent these scenarios from materializing or, if they do, to ensure they do not lead to the business’s collapse. In any case, the first requirement to protect your business is to know these risks and always keep them in mind.
Consider frequently reviewing existing threats and staying up to date on effective mechanisms to protect yourself. In many cases, having a trusted ally for your protection is a great idea.